Docker swarm setup is pretty straightforward but I had to deal with some network problems for Vultr during the setup, so this is a quick note to expose these problems and explain how to fix them.
A reminder about private network for Vultr instances
An important consideration for your Docker swarm configuration is that all your cloud instances must be within the same private network, Vultr supports this only if all instances are in the same region (US, UK, etc)
Create instances
Create your first instance through Vultr admin, if you want to make things faster and safer I recommend you to create an instance with Docker directly, in my case I prefer to use CentOS but you can also choose Ubuntu.
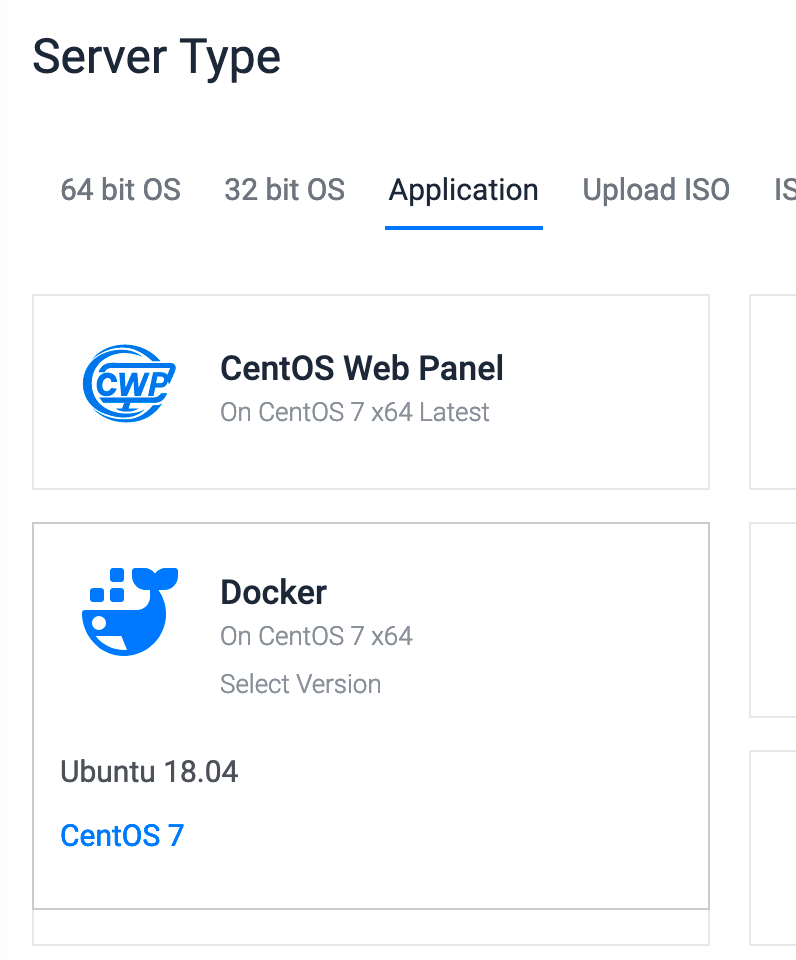
Enable private network checkbox, other checkboxes are not mandatory but it will depend on your needs.
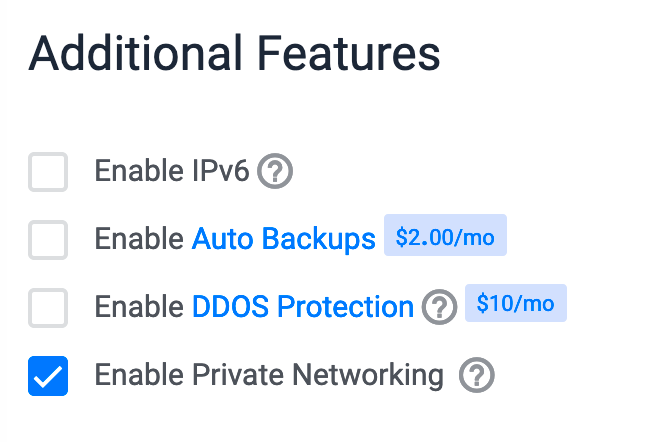
Done! By default Vultr firewall is disabled, anyway if you have an existing instance please ensure firewall is not enabled through Vultr admin, you can check this through (your instance) → Settings → Firewall
Follow the same steps for the second instance and remember to create it under the same region!
Now let's go with some configuration you need to perform in the new instances.
First you need to enable your private network interface, this step is well documented by Vultr https://www.vultr.com/docs/how-to-configure-a-private-network-on-centos
Firewall issues
If you are using CentOS there's a firewall enabled by default (firewalld) and all ports required by Docker swarm are blocked. This is a problem considering all worker instances need to contact port 2377 on the manager (main) instance.
How to solve it
The eth1 network interface configured previously through Vultr documentation steps will be added to the public zone by default, so the first thing we must do is to create a new zone and change the network interface to this new zone:
sudo firewall-cmd --permanent --zone=internal --change-interface=eth1Ensure the zone is active and contains the expected interfaces:
> firewall-cmd --get-active-zones
internal
interfaces: eth1
Now that we have the zone configured correctly, we can open ports for the internal network only and keep the public network safe. We open all ports required by Docker swarm:
firewall-cmd --add-port=2376/tcp --permanent --zone=internal
firewall-cmd --add-port=2377/tcp --permanent --zone=internal
firewall-cmd --add-port=7946/tcp --permanent --zone=internal
firewall-cmd --add-port=7946/udp --permanent --zone=internal
firewall-cmd --add-port=4789/udp --permanent --zone=internal
Finally, remember to reload the firewall to refresh these new rules
firewall-cmd --reloadAlternative solution for testing
If you still have some problems with your firewall configuration you can disable it through systemctl (`systemctl stop firewalld`), anyway this could be a risk for your server, so this is not the recommended way to fix the problem, but at least you have the chance to discard any configuration problem with the firewall.
Now you are ready to create your Docker swarm!
Go to the manager node first and run:
docker swarm initCopy the resulting join command, then go to your worker node and run that line.
That's all you need to get your Docker Swarm ready with Vultr.